In this post I walk you through how to validate an Oracle Identity Management build out containing OID, OVD, OIM, and OAM. This post was motivated by work I have done with Fusion Apps.
It is important to validate the IDM build out for Fusion Apps before you move on to the provisioning of Fusion Apps itself. Problems detected during the IDM build out are much easier to diagnose and fix than problems detected during FA provisioning, FA functional setup or FA operations themselves.
In addition, it is important to have documented validation steps for your Oracle IDM environment to use at other points as well. For instance, you will want to validate your IDM environment when you bring it back online following a backup.
Lastly, you will want to be able to go through validation steps for your IDM environment as a means of debugging IDM related application issues. For example, let’s say people come to you all of the sudden saying they can’t login to a Fusion HCM application. You’ll want to be able to go through the IDM validation steps to see what if anything is wrong with the IDM infrastructure that could be causing this issue.
Again, I wrote this with Fusion Apps in mind but everything here also applies to enterprise Oracle IDM build outs that use OID, OVD, OIM, and OAM. The only differences may be that for an enterprise deployment, the IDM services may be spread out across multiple WLS Domains and the system account being verified in the OID validation step may be different.
Recommended Validation Steps
The following are test cases for validating your IDM environment from bottom to top. We begin with just verifying that all services are running, move onto validating that the directory services are working, and then onto validating that OAM and OIM are working. We finish up with advanced but important tests that validate that SOA suite (the workflow provider for OIM) is working properly with OIM and that OAM/OIM integration is working.
These are descriptive test cases rather than fully documented click by click instructions. If you new to the Oracle IDM stack I encourage you to put in the time to flush this out into click by click instructions.
1) Verify all services are running. Login to IDM Domain admin server and ensure that all managed servers are up and running.
a. Go to environment --> Servers.
b. Make sure that the AdminServer and all 4 Managed Servers (OAM, OIM, SOA, and ODSM) are in Running state
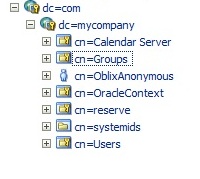
2) Verify ODSM and OID. Go to ODSM connect to OID and verify that you can see all users and JPS root (for policy data).
a. Go to ODSM: http://idmost.mycompany.com:7777/odsm
b. Click on Connect to a directory and choose OID
c. Go to Data Browser and verify the following folders under Root:
idm_jpsroot: this folder should look like this:
Make sure the following users are present:
Make sure the following groups are there:
f. For each one of the groups below, make sure user membership is as follows:
Groups | Members |
cn=IDM Administrator | cn=weblogic_idm |
cn=OAMAdministrators | cn=oamadmin |
cn=OIMAdminstrators | cn=oimldap |
cn=orclFAGroupReadPrivilegeGroup | cn=idrouser cn=oamldap |
cn=orclFAGroupWritePrivilegeGroup | cn=idrwuser |
cn=orclFAOAMUserWritePrivilegeGroup | cn=oamldap |
Cn=orclFAUserReadPrivilegeGroup | cn=idrouser cn=oamldap |
cn=orclFAUserWritePrefsPrivilegeGroup | cn=idrouser |
cn=orclFAUserWritePrivilegeGroup | cn=idrwuser |
cn=orclPolicyAndCredentialReadPrivilegeGroup | cn=policyrouser |
cn=orclPolicyAndCredentialWritePrivilegeGroup | cn=policyrwuser |